Authentication Using Symmetric Key Encryption
Mar 29, 2024
Article
Can we just be honest? Encryption, authentication and embedded systems security is hard—at least it can be for those of us not living and breathing that world. Thankfully, companies like Microchip provide products, tools and tutorials to make life easier when you need to incorporate these items into your embedded designs.
In this blog post I want to explain Symmetric Authentication between a host and a device and point you to a lab and video developed by Microchip showing how this is accomplished using Datakey CryptoAuthentication™ memory tokens.
Symmetric Authentication (or Symmetric Key Authentication or Symmetric Encryption) uses a single shared key that is used for encrypting and decrypting data. The key we are referring to here is not a physical key, but rather a string of numbers.
New concepts are often easier to learn if we can relate it to a real-world example, so we’ll do this here. Let’s say you work for a medical device manufacturer. You have an embedded controller unit (the host that has the brains) and a single use disposable that plugs into the host. The disposable may be a tubing set, a filter kit, a catheter, etc. Unlike the host, the disposable has no brains.
If you are familiar with the razor-razorblade business model, this is a common sales model for medical devices with disposables—“give away” the machine (the host with the brains) and make your money on the single-use disposables. Because the disposables are often relatively inexpensive to manufacturer, these turn out to be high-margin sales. This makes them targets for counterfeit devices from other manufacturers. To make sure knockoff devices won’t work with the host device, we are going to include a Datakey CryptoAuthentication memory token in with each (legit) disposable. In order for the machine to run, the operator must hook up the disposable and insert the memory token into the host, and the host will then determine whether the disposable is authentic.
For this example, we will use Symmetric Authentication to validate that the CryptoAuthentication memory token included in the disposable kit is authentic and can be trusted. Symmetric Authentication is a challenge/response process where the host (the medical device with the embedded controller) will challenge a device (in this case the Datakey CryptoAuthentication memory token included with the disposable). If the device is authentic, it must respond with the expected results.
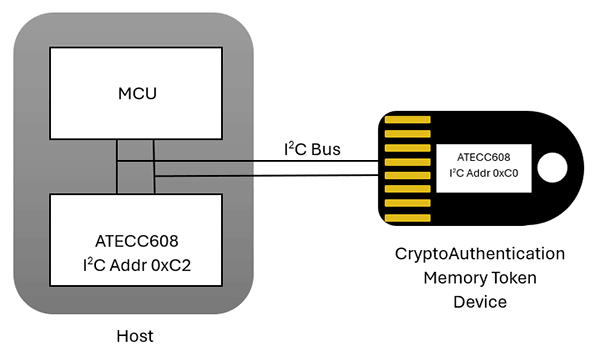
As mentioned above, Symmetric Authentication uses a shared key. That is, both the host and the device share the same secret key. Because this shared key must remain a secret, it is important to securely store this key on the host. A great way to do that is to use a Microchip CryptoAuthentication memory IC, like the ATECC608, on the host. This is the same IC that is found in the Datakey IAT10.5Kb CryptoAuthentication memory token. These ICs also have a unique, non-changeable serial number, which will also be leveraged in the symmetric authentication process. Microchip provides the CryptoAuthLib library, which is full of functions that we can leverage to simplify the authentication process. As we walk through the process, we’ll call out which function to use for each step.
Symmetric Authentication Process
When the memory token (shown on the right in the diagram above) is inserted into the host an interrupt is triggered indicating that a memory token has been detected. The authentication process can now begin.
- In the diagram above, you can see that the host microcontroller will be talking to two ATECC608 CryptoAuthentication memory ICs—one on the host and one in the memory token device. The CryptoAuthLib software running on the host needs to be initialized with information about the two ATECC608 ICs. This is done using the function atcab_init. atcab_init can be called repeatedly to select which IC (host or device) is being communicated with.
- The host starts the authentication process by asking the memory token device for its unique serial number. For this, we will use the function called atcab_read_serial_number.
- Now that the host knows the device’s serial number, it can send a challenge to the device. The challenge consists of three components:
- First, the host generates a random number that is used once. This is called a nonce (a number used once). To generate the random number, we will use the atcab_random function. Once the random number has been generated, it can be sent to the memory token device as a challenge.
- The second component that makes up the challenge is the shared secret key. Both the host and the device have the same secret key stored securely in their respective ATECC608 CryptoAuthentication ICs.
- The third component is the serial number of the memory token device. The host requested this information in Step 1, so both the host and the device can use the same three inputs.
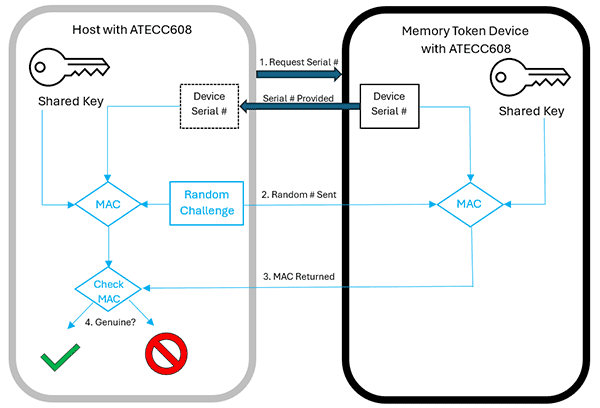
To send the challenge to the memory token device, the host will use the atcab_mac function. The MAC function computes a SHA-256 digest of the serial number, the challenge nonce (the random number) and the shared secret key. A digest is the output “signature” from a hashing function (in this case the SHA-256 hashing algorithm) for the data being hashed (in this case, the serial number, the challenge and the shared key). Let’s talk about the importance of these three items:
Serial Number
The serial number means that the digest will be specific to this particular memory token device. A memory token with a different serial number will produce a completely different digest.
Random Number
The random number, the challenge (on nonce), makes this challenge unique or fresh. Past or future challenges would use a different random number and would produce a different digest.
Shared Secret Key
In our medical disposable example, if a counterfeit device was smart enough to include a CryptoAuthentication memory token, it would be able to respond to the challenge, but the counterfeiters would not know the secret key, so it will not match the key on the host and it will produce a different digest value. Having the proper shared secret key is what indicates that the disposable (in this example) is genuine.
- The challenge is issued to the memory token device using the atcab_mac function and the device produces the digest and returns that value to the host. The value returned is called a Message Authentication Code (MAC).
- Now that the MAC has been returned, the host can now check to see if the MAC from the memory token device was correctly calculated. The host “knows” the same three inputs: the device’s serial number, the random number, and it has the same secret key. Since we want to check a MAC calculated by another device, we will use the atcab_checkmac function (rather than the atcab_mac function). The atcab_checkmac function computes the SHA-256 digest of the three inputs and compares it to the MAC returned from the device. The function returns either success (they match) or fail (they do not match). Success indicates that the disposable in our example is genuine and can be trusted.
We just confirmed that we have a genuine disposable, but how do we know that this disposable (or the memory token) hasn’t already been used? A CryptoAuthentication memory token can address that issue as well, but we’ll leave that topic for another day.
The discussion in this blog article was based on LAB 1 – Symmetric Authentication of a Remote Device, which is covered in the Microchip lab manual titled, “Developing Secure Applications with CryptoAuthentication Devices”. This Microchip-developed lab has been modified to be used with Datakey CryptoAuthentication memory tokens. For more information on this lab and to watch a video covering which hardware and software is needed and how to get it properly configured, please check out the how-to page: Using CryptoAuthentication Memory Tokens with Microchip Quick Start Lab.
For more information on Datakey CryptoAuthentication memory tokens and related products, please check our CryptoAuthentication product page. If you have any questions or comments on this blog article or Datakey CryptoAuthentication memory tokens, please contact us.
CryptoAuthentication is a trademark of Microchip Technology Incorporated in the U.S.A. and other countries and is used under license.